How confident are you that your defenses would catch a ransomware payload buried three layers deep in a fake document?
Attackers are getting better at hiding malicious behavior, using loaders, phishing lures, and delayed execution to quietly bypass traditional detection. For security teams, that means threats often stay invisible until it’s too late.
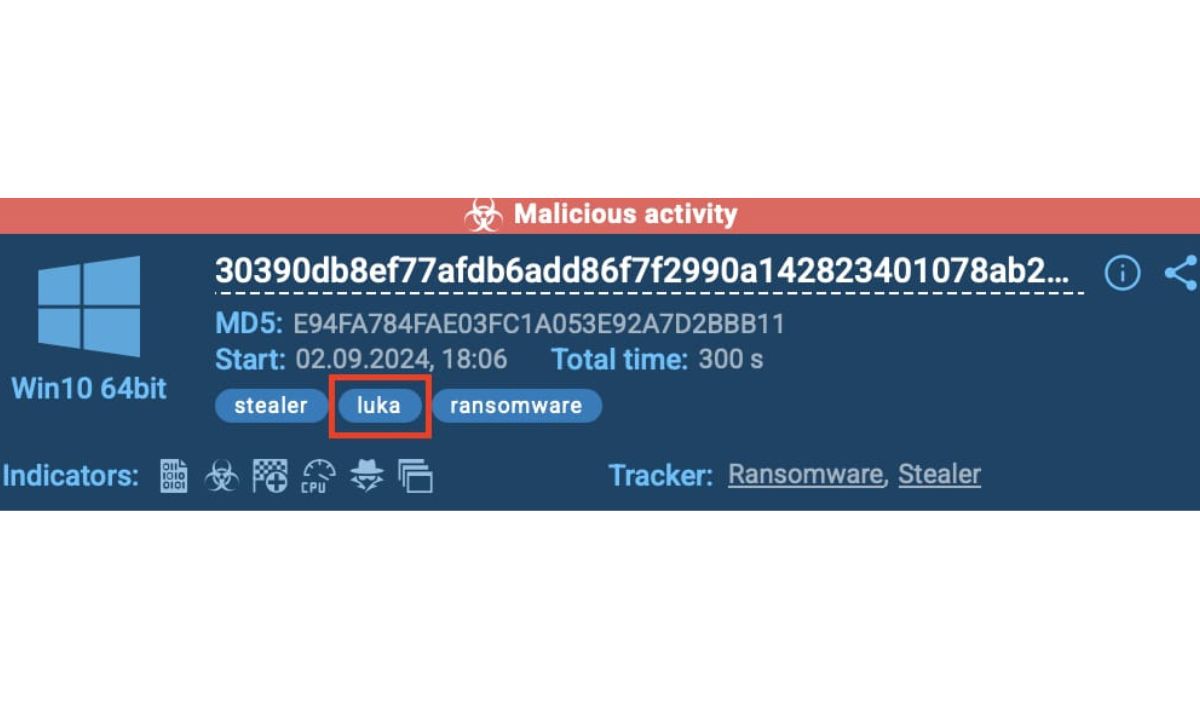
Three emerging ransomware families, Mamona, Devman, and Nitrogen, are leading this shift. Each one uses different tactics to evade automated tools and blend into legitimate traffic, but the outcome is the same: encryption, extortion, and stolen data.
Here’s what your SOC needs to know about them!
Mamona: Offline Commodity Ransomware with Low Detection Footprint
Mamona is a new ransomware strain making the rounds in the cybercrime scene. It’s part of a growing trend of commodity ransomware; malware created using builder kits that are leaked or sold online, allowing anyone to generate their own variant without writing a single line of code.
What makes Mamona tricky is that it works entirely offline. Unlike most ransomware, it doesn’t talk to a command-and-control server or try to exfiltrate data. It simply encrypts local files and drops a ransom note, threatening to leak stolen data.
Many detection tools rely on spotting suspicious network traffic or calls to known malware infrastructure. Mamona avoids both. As soon as it runs, it performs a fake delay using a loopback ping (127.0.0.7), then tries to delete itself to cover its tracks. This behavior doesn’t raise red flags in static scans or network logs. It looks almost like normal system activity.
This is where interactive analysis makes a big difference. Inside an interactive sandbox, such as ANY.RUN, Mamona’s full behavior is triggered and recorded in real time.
View Mamona in action in a live analysis session
You can clearly see:
- The fake “ping” delay used to avoid detection
- The self-deletion command meant to erase evidence
- How it drops ransom notes across multiple folders
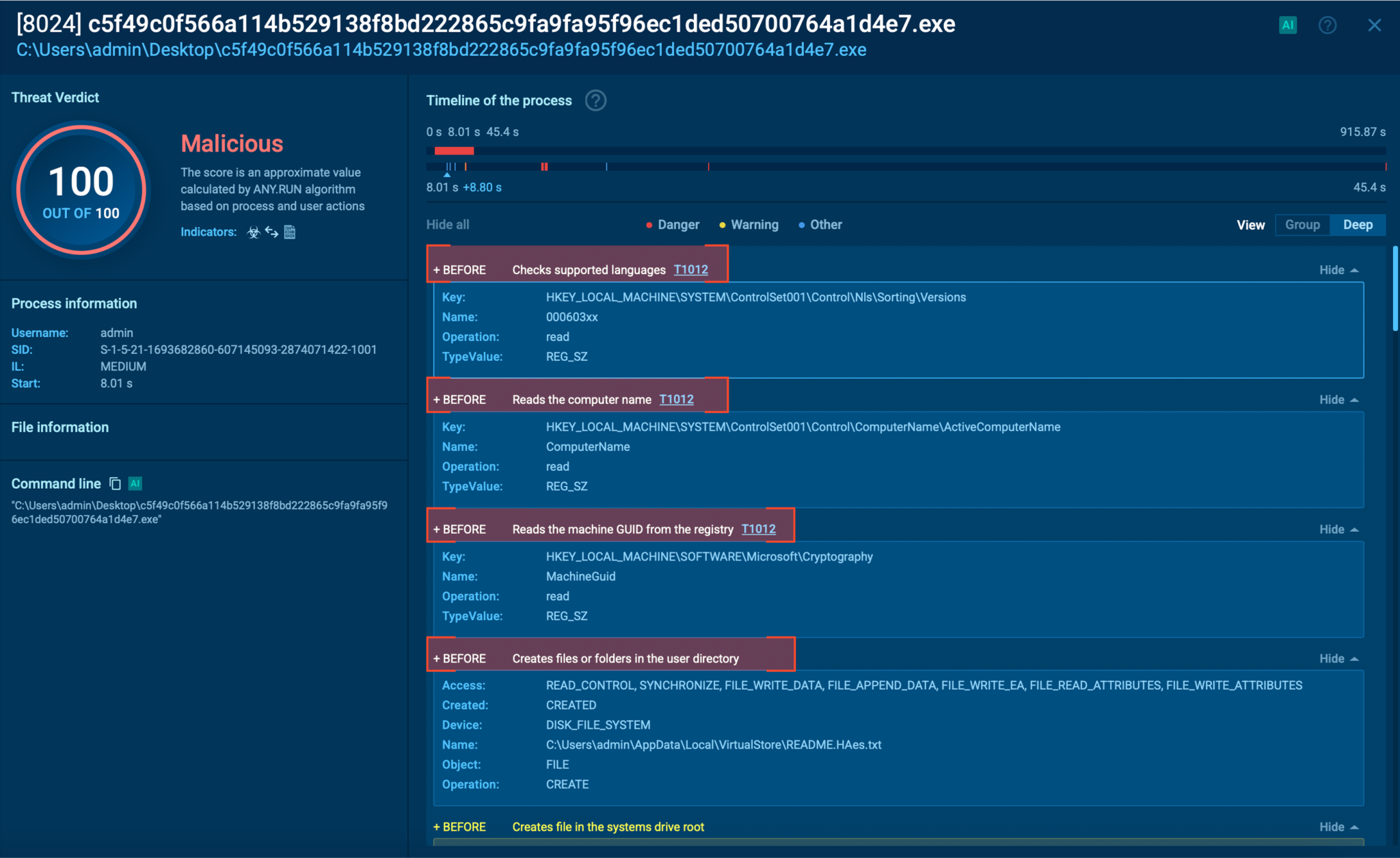
Ransom note dropping exposed inside ANY.RUN sandbox
- How it renames encrypted files with a .HAes extension
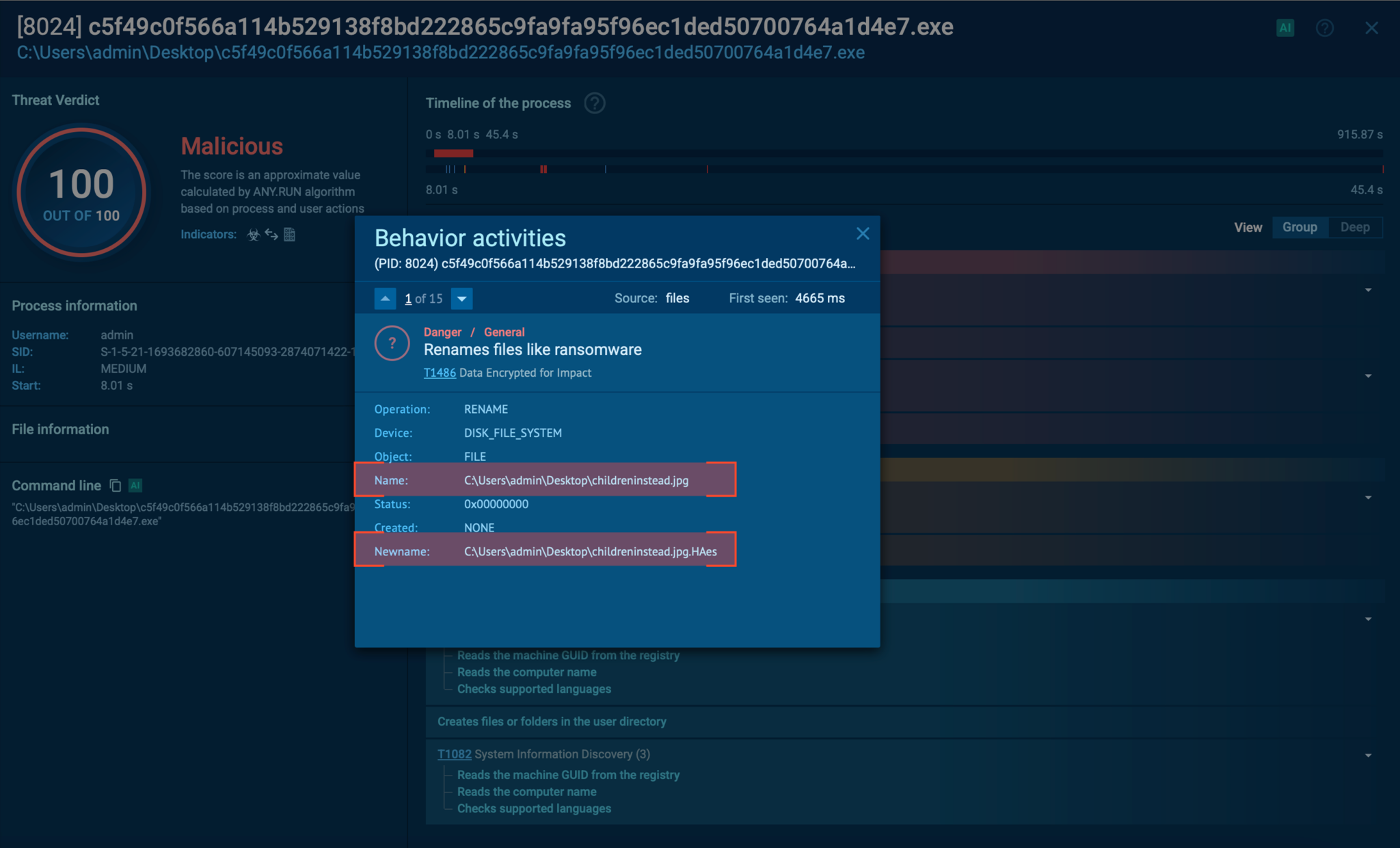
The file was encrypted and renamed with .HAes extension
With automated interactivity, your team doesn’t need to manually test every suspicious file. You can integrate sandbox analysis into your workflow using API and automatically uncover the full attack chain, even when it’s hiding inside a phishing email attachment.
| Give your SOC the visibility it needs with automated analysis, real-time behavior tracking, and full attack chain detection. Try ANY.RUN Now |
DEVMAN: A New Variant of DragonForce
Not all new ransomware strains are built from scratch. DEVMAN appears to be a rework of DragonForce, which itself is based on the older Conti codebase. But this is a strange hybrid that introduces its own quirks, from file renaming patterns to encrypted ransom notes.
Most of DEVMAN’s activity also takes place entirely offline, with no network communication during execution. That means network-based tools won’t raise any alerts, and static scans may miss the deeper behavioral patterns altogether.
Inside an interactive sandbox like ANY.RUN, however, these traits come into focus. Even flawed or half-functional samples reveal a full picture when the environment reacts like a real machine.
Once executed, DEVMAN begins encrypting user data and renaming files with the .DEVMAN extension. Even ransom notes are affected, scrambled and unreadable due to a flaw in the builder.
Inside ANY.RUN, every file action is captured in real time, helping analysts clearly trace the attack chain, extract IOCs, and understand the full scope of impact, cutting down investigation time and improving response accuracy.
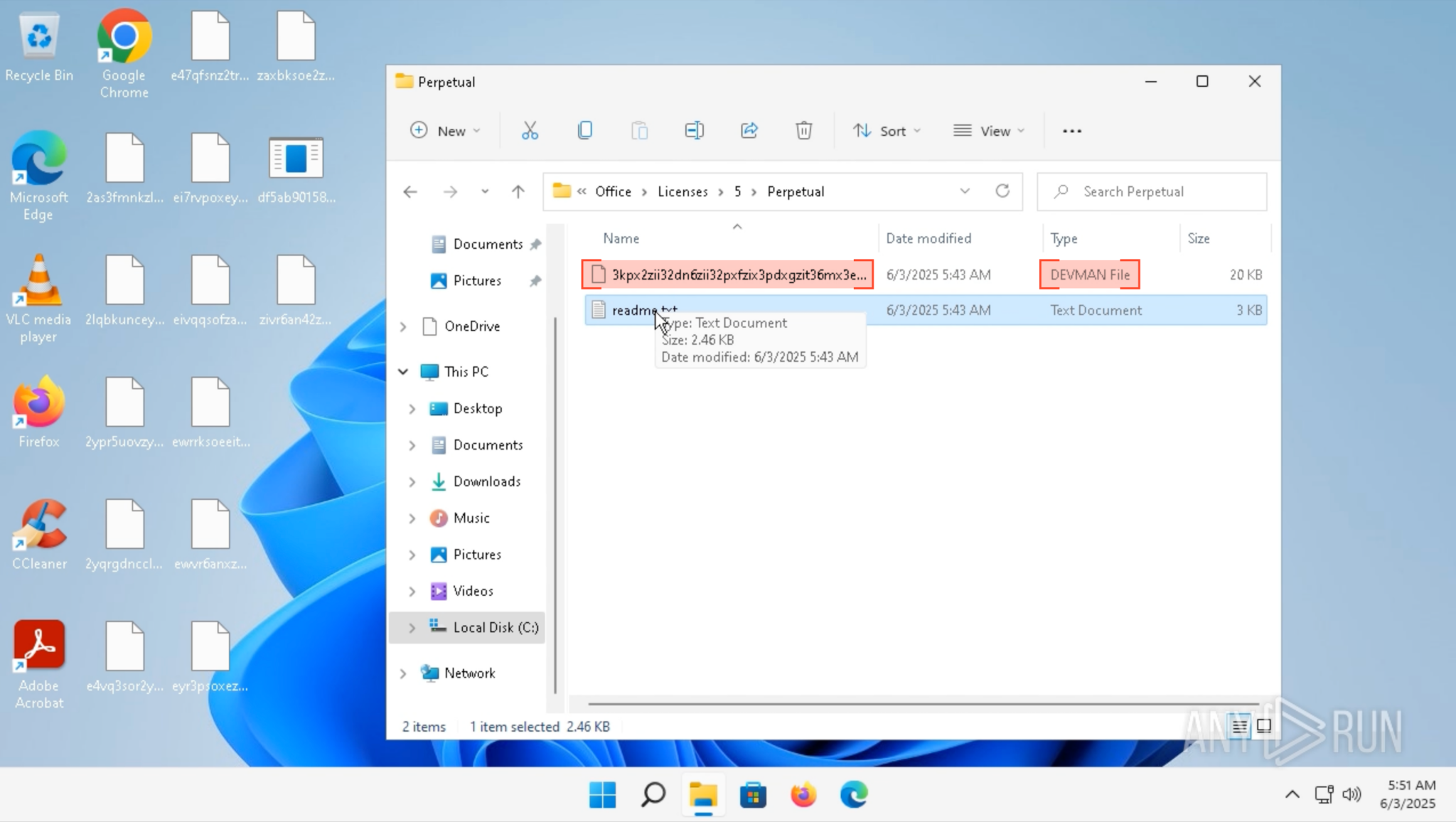
Encrypted file with the .DEVMAN extension inside ANY.RUN sandbox
DEVMAN attempts to swap the desktop background with a ransom warning, but behavior isn’t consistent. The change succeeds on Windows 10 but fails silently on Windows 11, revealing gaps in attacker testing.
With ANY.RUN’s support for multiple environments (Windows, Linux, and Android), teams can easily analyze similar threats across OS variants, spot inconsistencies, and proactively defend against platform-specific tactics.
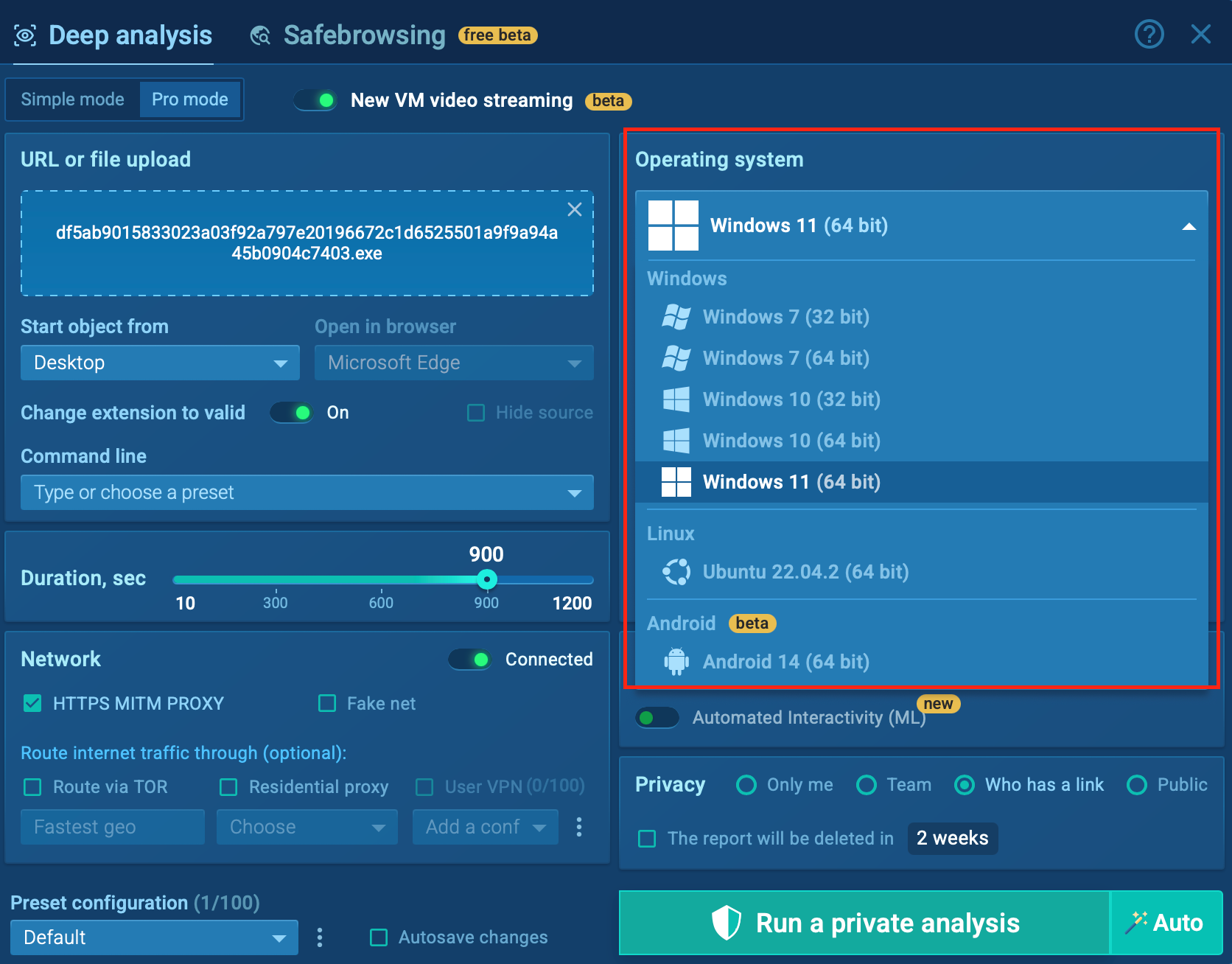
Analyzing the same threat in multiple environments for the best results
To ensure files are encrypted, even those in use, DEVMAN interacts with the Windows Restart Manager, a known technique carried over from Conti and DragonForce. It also creates multiple mutexes to manage its execution and avoid conflicts.
In ANY.RUN’s sandbox, these operations are surfaced automatically, revealing how the malware bypasses file locks and avoids detection. This level of insight allows SOC teams to quickly identify advanced techniques that traditional tools might overlook.
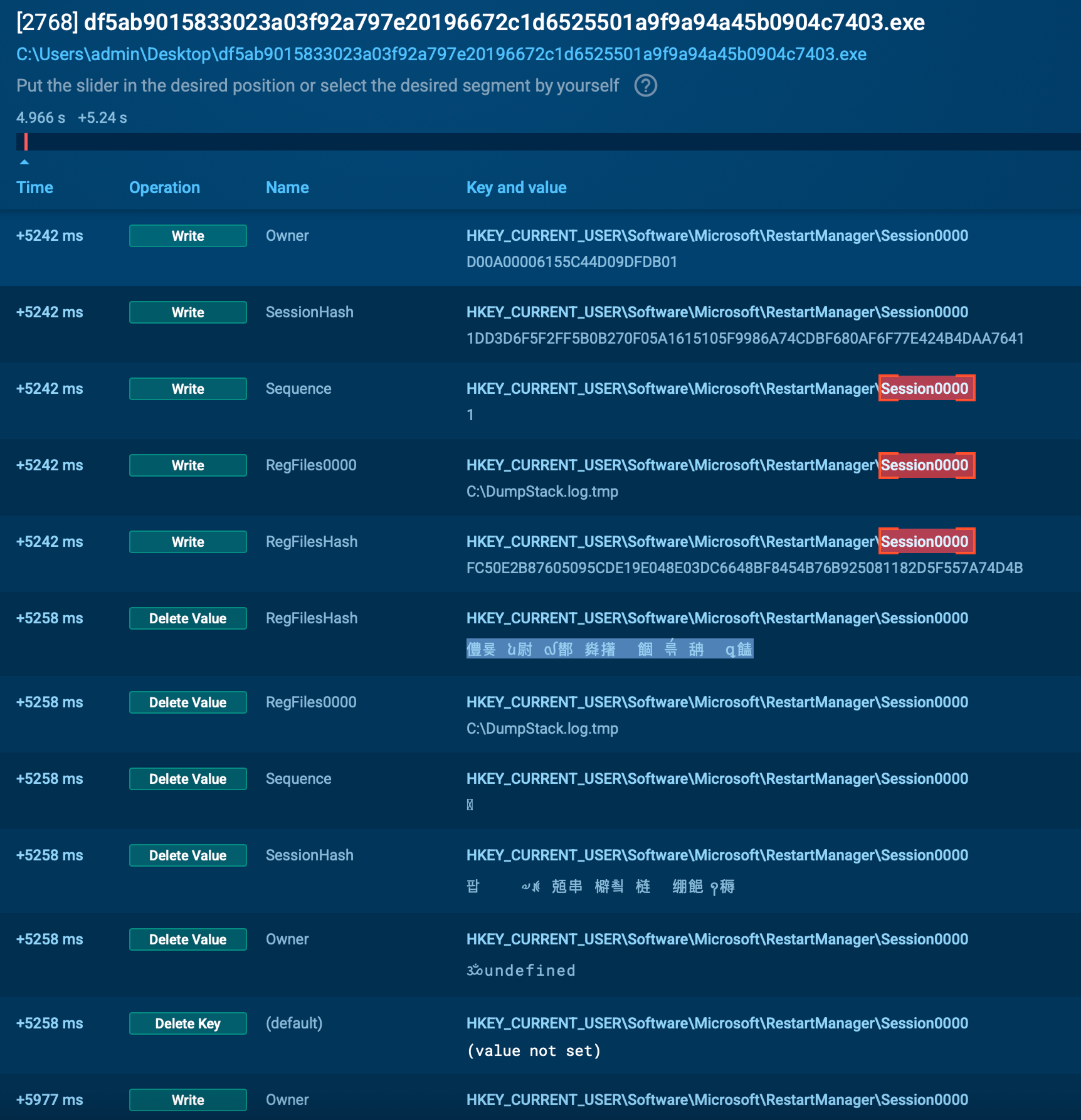
Regkeys altered by the sample inside ANY.RUN sandbox
Nitrogen: A Stealthy Operator with Serious Impact
Nitrogen is a relatively new ransomware strain that gained traction in late 2024, targeting industries like finance, tech, construction, and manufacturing across the U.S., Canada, and the U.K. One of its most notable victims, SRP Federal Credit Union, suffered an attack in December 2024, highlighting Nitrogen’s reach and real-world damage.
What makes Nitrogen particularly dangerous is its quiet, layered approach: it disables security tools, blocks recovery, and encrypts files using techniques that closely resemble other threats like LukaLocker. While public reports on Nitrogen are limited, interactive sandbox analysis sheds light on its full behavior, revealing tactics that would otherwise stay hidden.
Let’s break down three of its most critical actions inside the sandbox.
While public research on Nitrogen is still limited, analysis inside the ANY.RUN sandbox reveals key behaviors that paint a much clearer picture. We can observe the full attack chain in action: from system manipulation to the ransom note dropped on the desktop, clearly displayed during the simulation.
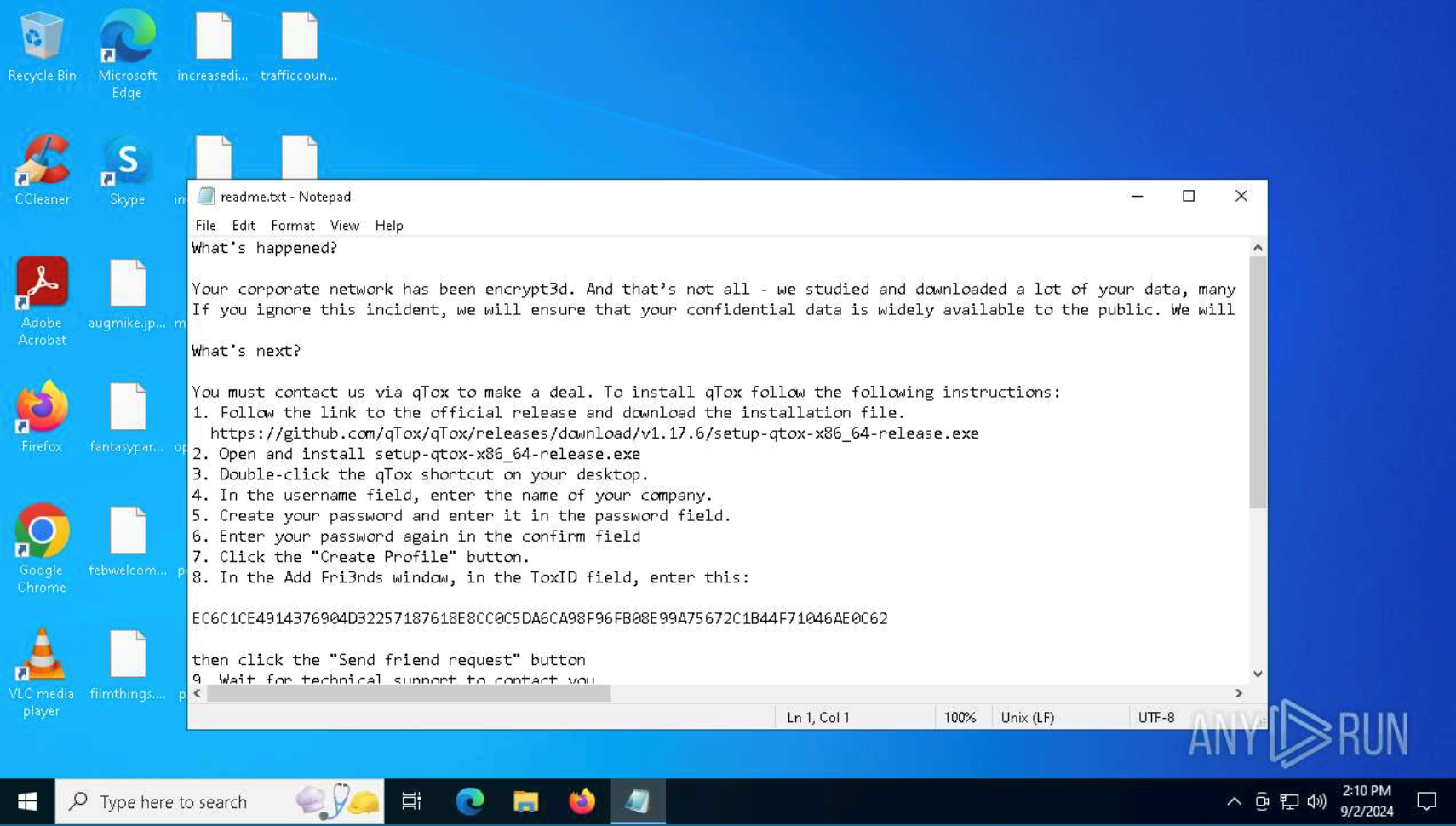
Ransom note dropped by Nitrogen inside ANY.RUN sandbox
What’s more, the sandbox automatically links Nitrogen to LukaLocker, uncovering code similarities and shared encryption behavior.
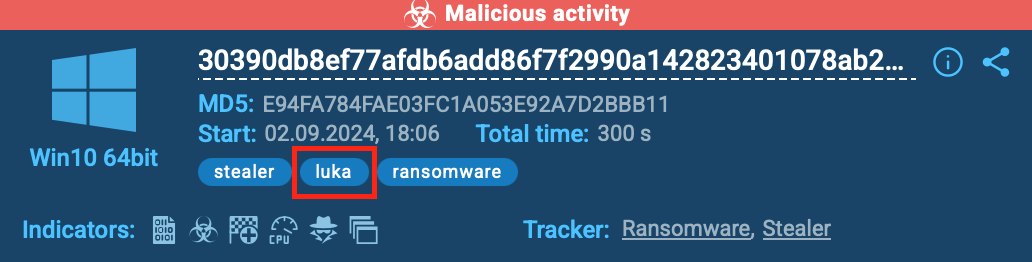
Nitrogen having similarities and shared encryption behavior with LukaLocker
ANY.RUN reveals the full encryption sequence, file modifications, and ransom note creation in real time, exposing the malware’s code structure and behavior with clarity.
This insight helps teams connect the dots between related threats and strengthen detection rules based on behavior, not just static signatures.
Uncover Hidden Threats and Automate Your Malware Analysis Workflow
Ransomware strains like Mamona, DEVMAN, and Nitrogen are built to bypass traditional detection, hiding in phishing attachments, abusing legitimate tools, and delaying execution until it’s too late. But inside an interactive sandbox, their tactics are exposed step by step, no matter how deeply they’re buried.
With ANY.RUN, security teams can go beyond static scans and automate full behavioral analysis using API and Automated Interactivity. Suspicious files and URLs are executed in real time, simulating user actions to trigger hidden behavior, so threats don’t slip through the cracks.
For SOC teams, this means:
- Faster detection of evasive ransomware and loaders
- Clear visibility into full attack chains, even offline threats
- Early identification of persistence techniques and encryption routines
- Support for multiple OS environments to catch OS-specific behavior
- Streamlined investigations and enriched IOC extraction
- Seamless integration into SIEMs, SOARs, and threat hunting workflows
Start your 14-day trial of ANY.RUN and give your team the tools to stay ahead of emerging threats.
ALSO READ: Figgs AI: Revolutionizing Smart Business Intelligence